However Hayden, a four-star general who is now retired, does not deny that the NSA is involved in espionage.
"We steal secrets. We're number one in it," he says.
" But, he adds, this is not malicious or industrial espionage.
"We steal stuff to make you safe, not to make you rich."
(later take look at opencatalog.darpa.mil/ and sites like nsaplayset.org/openproblems (fallow wiki related links) by hobbyist, if .mil sites look to spooky to visit. )
This is a list of Known government surveillance projects and related databases throughout the world.
- ECHELON: A signals intelligence (SIGINT) collection and analysis network operated on behalf of the five signatory states to the UKUSA Security Agreement.
- Data Retention Directive: A directive requiring EU member states to store citizens' telecommunications data for six to 24 months and allowing police and security agencies to request access from a court to details such as IP address and time of use of every email, phone call, and text message sent or received.
- INDECT: Research project funded by the European Union to develop surveillance methods (e.g. processing of CCTV camera data streams) for the monitoring of abnormal behaviours in an urban environment.[1]
- Schengen Information System: A database kept for national security and law enforcement purposes.
- In August 2014 it was reported[2] that law-enforcement agencies had been accessing Australians' web browsing histories via internet providers such as Telstra without a warrant.
- It was reported[3] that Australia had issued 75% more wiretap warrants in 2003 than the US did and this was 26 times greater than the US on a per capita basis.
- Golden Shield Project: Also known as the "Great Firewall of China", it is a censorship and surveillance project operated by the Ministry of Public Security (MPS) division of the government of the People's Republic of China. The project was initiated in 1998 and began operations in November 2003.[4]
- Monitoring Bureau[4]
- Public Information Network Security[4]
- Frenchelon: A data collection and analysis network operated by the French Directorate-General for External Security.[5]
- Nachrichtendienstliches Informationssystem: a searchable database operated by the German security agency Bundesamt für Verfassungsschutz (BfV).[6]
- Project 6: a global surveillance project jointly operated by the German intelligence agencies Bundesnachrichtendienst (BND) and Bundesamt für Verfassungsschutz (BfV) in close cooperation with the U.S. Central Intelligence Agency (CIA).[7]
- Central Monitoring System (CMS): A data collection system similar to the NSA's PRISM program.[8] It enables the Government of India to listen to phone conversations, intercept e-mails and text messages, monitor posts on social networking service and track searches on Google.[9]
- DRDO NETRA: Network that is capable of tracking online communications on a real time basis by harvesting data from various voice-over-IP services, including Skype and Google Talk. It is operated by the Research and Analysis Wing.
- NATGRID: An intelligence grid that links the databases of several departments and ministries of the Government of India.
- SORM: A technical system used by the Federal Security Service of the Russian Federation to monitor internet and telephone communication.
- Yarovaya Law is a anti-terrorist legislation that includes requirement to store all voice and text messaging data, as well as providing cryptographic backdoors for security services.
- Titan traffic database: A database established by the Swedish National Defence Radio Establishment where call detail records (CDRs) of telephony and internet traffic and transaction data (IPDRs) concerning international telecommunications are stored.[citation needed]
- X-Keyscore: A system used by the United States National Security Agency for searching and analysing internet data about foreign nationals. FRA has been granted access to the program. Template:Http://www.svt.se/ug/article1666993.svt
- Onyx: A data gathering system maintained by several Swiss intelligence agencies to monitor military and civilian communications, such as e-mails, telefax and telephone calls. In 2001, Onyx received its second nomination for the ironically-named "Big Brother Award".[10]
- Impact Nominal Index: The Impact Nominal Index or INI is a computer system that enables the UK police force to establish whether other relevant authorities are holding information regarding a person of interest.[11]
- Interception Modernisation Programme: An initiative to extend the UK government's capability to lawfully intercept and store communications data in a central database.[12]
- Mastering the Internet (MTI): A clandestine mass surveillance program led by the British intelligence agency GCHQ. Data gathered by the GCHQ include the contents of email messages, entries on the social networking platform Facebook and the web browsing history of internet users.[13]
- UK National DNA Database (NDNAD): It is also the oldest national DNA database in the world.[14] Since its establishment in 1995, the database has grown to include DNA samples from 2.7 million individuals, or 5.2% of the UK's population, many of whom have neither been charged with, or convicted of, any offense (// but in reality... nearly everyone's are saved for another species..).[14]
- Tempora: Launched in the autumn of 2011, this initiative allows the GCHQ to set up a large-scale buffer that is capable of storing internet content for 3 days and metadata for 30 days.[15]
- Royal Concierge: prototyped in 2010, sends daily alerts to GCHQ whenever a booking is made from a ".gov." second-level domain at select hotels worldwide.[16]
- Boundless Informant: A system deployed by the National Security Agency to analyze global electronic information. In March 2013, Boundless Informant gathered 14 billion data reports from Iran, 6.3 billion from India, and 2.8 billion from the United States.[17]
- BULLRUN: a highly classified U.S. National Security Agency program to preserve its ability to eavesdrop on encrypted communications by influencing and weakening encryption standards, by obtaining master encryption keys, and by gaining access to data before or after it is encrypted either by agreement, by force of law, or by computer network exploitation (hacking).
- Carnivore: A system implemented by the Federal Bureau of Investigation that was designed to monitor email and electronic communications. Apparently replaced by commercial software such as NarusInsight.
- Comprehensive National Cybersecurity Initiative
- DCSNet: The Federal Bureau of Investigation (FBI)'s point-and-click surveillance system that can perform instant wiretaps on any telecommunications device located in the United States.[18]
- Fairview: A mass surveillance program directed at foreign mobile phone users.
- Financial Crimes Enforcement Network: A bureau of the Department of the Treasury that collects and analyzes financial transactions in order to combat financial crimes.
- ICREACH: Surveillance frontend GUI that is shared with 23 government agencies, including the CIA, DEA, and FBI, to search illegally collected personal records.
- Magic Lantern: A keystroke logging software deployed by the FBI in the form of an e-mail attachment. When activated, it acts as a trojan horse and allows the FBI to decrypt user communications.[19]
- Main Core: A personal and financial database storing information of millions of U.S. citizens believed to be threats to national security.[20] The data mostly comes from the NSA, FBI, CIA, as well as other government sources.[20]
- MAINWAY: NSA database containing metadata for hundreds of billions of telephone calls made through the four largest telephone carriers in the United States.
- MUSCULAR: Overseas wiretapping of Google's and Yahoo's unencrypted internal networks by the NSA.
- MYSTIC is a voice interception program used by the National Security Agency.
- Nationwide Suspicious Activity Reporting Initiative: Under this government initiative, a Suspicious Activity Report (SAR) may be filed by law enforcers, public safety personnel, owners of critical infrastructure or the general public.
- NSA ANT catalog: a 50-page document listing technology available to the United States National Security Agency (NSA) ANT division to aid in cyber-surveillance.
- PRISM: A clandestine national security electronic surveillance program operated by the United States National Security Agency (NSA) which can target customers of participating corporations outside or inside the United States.
- Room 641A: A telecommunication interception facility operated by AT&T for the U.S. National Security Agency.
- Sentry Eagle: efforts to monitor and attack an adversary's cyberspace through capabilities include SIGINT, Computer Network Exploitation (CNE), Information Assurance, Computer Network Defense (CND), Network Warfare, and Computer Network Attack (CNA). The efforts included weakening US commercial encryption systems.[21]
- Special Collection Service (SCS): A black budget program that is responsible for "close surveillance, burglary, wiretapping, breaking and entering." It employs covert listening device technologies to bug foreign embassies, communications centers, computer facilities, fiber-optic networks, and government installations.[22]
- Stellar Wind (code name): The open secret code name for four surveillance programs.
- Tailored Access Operations: Intelligence-gathering unit of the NSA that is capable of harvesting approximately 2 petabytes of data per hour.[23][24]
- Terrorist Finance Tracking Program: A joint initiative run by the CIA and the Department of the Treasury to access the SWIFT (Society for Worldwide Interbank Financial Telecommunication) transaction database as part of the Bush administration's "Global War on Terrorism". According to the U.S. government, its efforts to counter terrorist activities were compromised after the existence of the Terrorist Finance Tracking Program was leaked to the media.[25]
- Turbulance (NSA): Turbulence is a United States National Security Agency (NSA) information-technology project started circa 2005. It was developed in small, inexpensive "test" pieces rather than one grand plan like its failed predecessor, the Trailblazer Project. It also includes offensive cyberwarfare capabilities, like injecting malware into remote computers. The U.S. Congress criticized the project in 2007 for having similar bureaucratic problems as the Trailblazer Project.[26]
- US Intelligence Community (IC): A cooperative federation of 16 government agencies working together, but also separately, to gather intelligence and conduct espionage.
- Utah Data Center: The Intelligence Community's US$1.5 billion data storage center that is designed to store extremely large amounts of data, on the scale of yottabytes.[27][28][29]
- X-Keyscore: A system used by the United States National Security Agency for searching and analysing internet data about foreign nationals.
- GhostNet: A fictitious code name given to a large-scale surveillance project that is believed to be operated by the People's Republic of China.[30]
- Stuxnet: It is the first discovered malware that spies on industrial systems, and it was used to attack Iran's nuclear facilities.[31] It is believed to have originated from the United States under the Bush administration.[32]
- Information Awareness Office: An office established to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other threats to U.S. national security.
- Multistate Anti-Terrorism Information Exchange (MATRIX): A data mining system originally developed for the Florida Department of Law Enforcement.
- Terrorist Surveillance Program: Replaced by PRISM.
- ThinThread: A U.S. National Security Agency (NSA) program involved wiretapping and sophisticated analysis of the resulting data.
- Trailblazer Project: U.S. National Security Agency (NSA) program intended to develop a capability to analyze data carried on communications networks including cell phone networks and the Interne
European Union
National
Australia
Main article: Mass surveillance in Australia
China
Main article: Mass surveillance in China
France
Germany
India
Further information: Mass surveillance in India
Russia
Sweden
Switzerland
United Kingdom
Further information: Mass surveillance in the United Kingdom
United States
 National Security Agency surveillance |
|---|

|
Further information: Mass surveillance in the United States
A top secret document leaked by Edward Snowden to The Guardian in 2013, originally due to be declassified on 12 April 2038.
Unclear origin
Recently discontinued
Updated from: https://en.wikipedia.org/wiki/List_of_government_mass_surveillance_projects
--------
Full listing: https://www.eff.org/files/2014/01/06/20131230-appelbaum-nsa_ant_catalog.pdf (Declassified on Jan. 8, 2032, mirror https://fveydocs.org/document/nsa-ant-catalog/)
NSA basic known software:
- The NSA ANT document contains codeword references to hardware and software surveillance technology available to the NSA.[18]
- BULLDOZER: Technology that creates a hidden wireless bridge allowing NSA personnel to remotely control a system wirelessly.[15][19]
- CANDYGRAM: A $40,000 tripwire device that emulates a GSM cellphone tower.
- COTTONMOUTH-I
- COTTONMOUTH: (see image at right) A family of modified USB and Ethernet connectors that can be used to install Trojan horse software and work as wireless bridges, providing covert remote access to the target machine.[20] COTTONMOUTH-I is a USB plug that uses TRINITY as digital core and HOWLERMONKEY as RF transceiver. Cost in 2008 was slightly above $1M for 50 units.
- COTTONMOUTH-II is deployed in a USB socket (rather than plug), and
costs only $200K per 50 units, but requires further integration in the
target machine to turn into a deployed system.

- COTTONMOUTH-III is a stacked Ethernet and USB plug costing approximately $1.25M for 50 units.
- CROSSBEAM is "a GSM communications module capable of collecting and compressing voice data" [21]
- CTX4000: Continuous wave radar device that can ""illuminate" a target system for recovery of "off net" information.[22]
- CYCLONE-HX9 - GSM Base Station Router
- DEITYBOUNCE: Technology that installs a backdoor software implant on Dell PowerEdge servers via the motherboard BIOS and RAID controller(s).[23][24]
- DROPOUTJEEP: "A software implant for the Apple iPhone that utilizes modular mission applications to provide specific SIGINT functionality. This functionality includes the ability to remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc. Command, control and data exfiltration can occur over SMS messaging or a GPRS data connection. All communications with the implant will be covert and encrypted."[8]
- EBSR is a "tri-band active GSM base station with internal 802.11/GPS/handset capability" [25]
- ENTOURAGE

- FEEDTROUGH: Software that can penetrate Juniper Networks firewalls allowing other NSA-deployed software to be installed on mainframe computers.[1][9][26]
- FIREWALK

- FIREWALK: (see image at right) A device that looks identical to a standard RJ45 socket that allows data to be injected, or monitored and transmitted via radio technology.[27] using the HOWLERMONKEY RF transceiver. It can for instance create a VPN to the target computer. Cost in 2008: $537K for 50 units.
- FOXACID: Technology that can install spyware using a "quantum insert" capable of infecting spyware at a packet level. (Not numbered because FOXACID may or may not be part of the NSA ANT catalog; sources differ.).
Finding machines that are exploitable and worth attacking is done using analytic databases such as XKeyscore.[21] A specific method of finding vulnerable machines is interception of Windows Error Reporting traffic, which is logged into XKeyscore.
QUANTUM attacks launched from NSA sites can be too slow for some combinations of targets and services as they essentially try exploit a race condition, i.e. the NSA server is trying to beat the legitimate server with its response.[23] As of mid-2011, the NSA was prototyping a capability codenamed QFIRE, which involved embedding their exploit-dispensing servers in virtual machines (running on VMware ESX) hosted closer to the target, in the so-called Special Collection Sites (SCS) network worldwide.
COMMENDEER is used to commandeer (i.e. compromise) untargeted computer systems. The software is used as a part of QUANTUMNATION, which also includes the software vulnerability scanner VALIDATOR.
QUANTUMCOOKIE is a more complex form of attack which can be used against Tor users
- FOXACID: Technology that can install spyware using a "quantum insert" capable of infecting spyware at a packet level. (Not numbered because FOXACID may or may not be part of the NSA ANT catalog; sources differ.).
- GENESIS

- GINSU: Technology that uses a PCI bus device in a computer, and can reinstall itself upon system boot-up.[28]
- GOPHERSET: GSM software that uses a phone's SIM card’s API (SIM Toolkit or STK) to control the phone through remotely sent commands.[29]
- GOURMETTROUGH: User-configurable persistence implant for certain Juniper Networks firewalls.[22]
- HALLUXWATER: Back door exploit for Huawei Eudemon firewalls.[22]
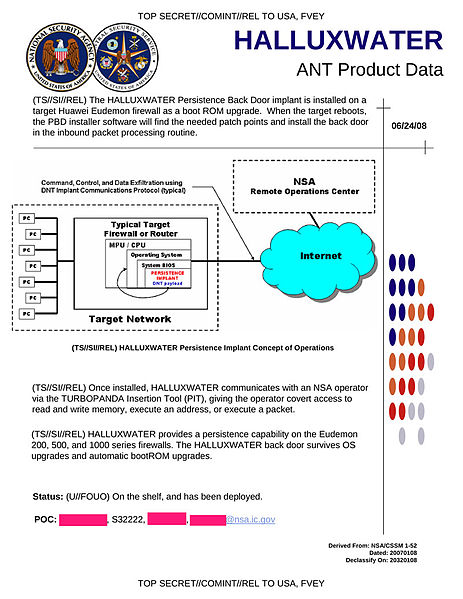
- HEADWATER: Persistent backdoor technology that can install spyware using a "quantum insert" capable of infecting spyware at a packet level on Huawei routers.[22]
- HOWLERMONKEY

- HOWLERMONKEY: (see image at right) A RF transceiver that makes it possible (in conjunction with digital processors and various implanting methods) to extract data from systems or allow them to be controlled remotely.
- IRATEMONK: Technology that can infiltrate the firmware of hard drives manufactured by Maxtor, Samsung, Seagate, and Western Digital.[30]
- IRONCHEF: Technology that can "infect" networks by installing itself in a computer I/O BIOS.[15] IRONCHEF includes also "Straitbizarre" and "Unitedrake" which have been linked to the gov spy software REGIN.
- JUNIORMINT

- JETPLOW: Firmware that can be implant to create a permanent backdoor in a Cisco PIX series and ASA firewalls.[22]
- LOUDAUTO: $30 audio-based RF retro-reflector listening device.[22]
- TRINITY

- MAESTRO-II: a multi-chip module approximately the size of a dime that serves as the hardware core of several other products. The module contains a 66 MHz ARM7 processor, 4 MB of flash, 8 MB of RAM, and a FPGA with 500,000 gates. Unit cost: $3–4K (in 2008). It replaces the previous generation modules which were based on the HC12 microcontroller.
- MONKEYCALENDAR: Software that transmits a mobile phone's location by hidden text message.
- NEBULA

- NIGHTSTAND: Portable system that wirelessly installs Microsoft Windows exploits from a distance of up to eight miles.[22]
- NIGHTWATCH: Portable computer used to reconstruct and display video data from VAGRANT signals; used in conjunction with a radar source like the CTX4000 to illuminate the target in order to receive data from it.
- PICASSO: Software that can collect mobile phone location date, call metadata, access the phone’s microphone to eavesdrop on nearby conversations.[29]
- PHOTOANGLO: A joint NSA/GCHQ project to develop a radar system to replace CTX4000.[22]
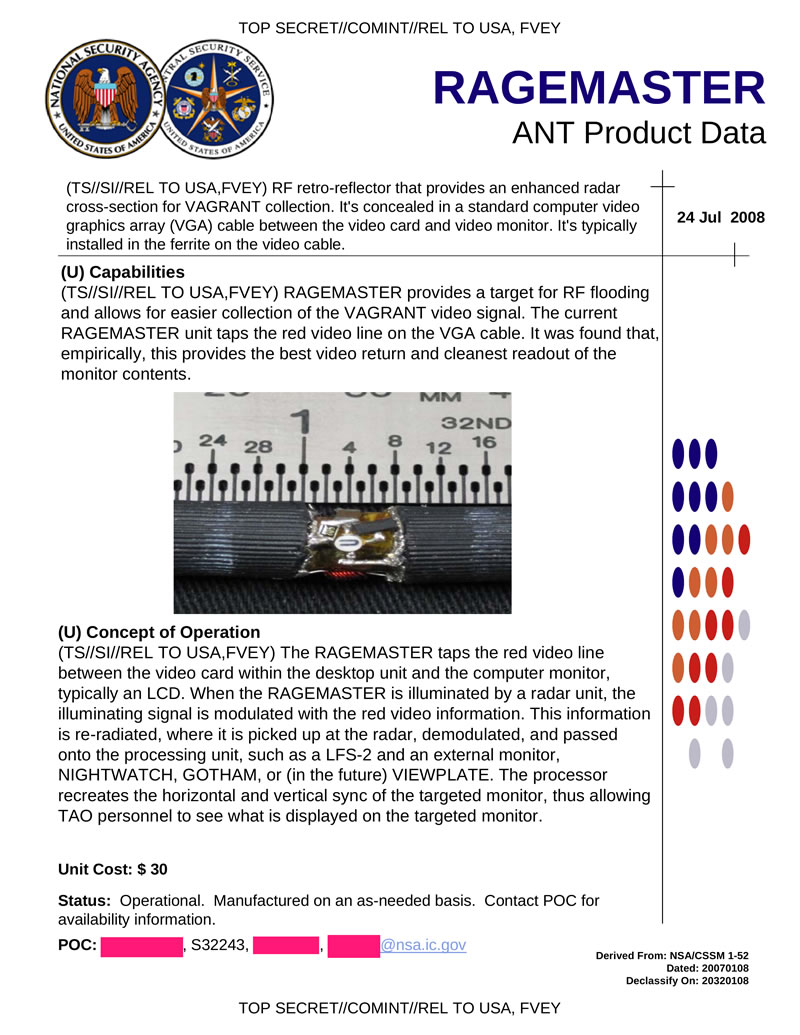
- RAGEMASTER: (see image above, right) A concealed $30 device that taps the video signal from a target's computer's VGA
signal output so the NSA can see what is on a targeted desktop monitor.
It is powered by a remote radar and responds by modulating the VGA red
signal (which is also sent out most DVI
ports) into the RF signal it re-radiates; this method of transmission
is codenamed VAGRANT. RAGEMASTER is usually installed/concealed in the ferrite choke
of the target cable. The original documents are dated 2008-07-24.
Several receiver/demodulating devices are available, e.g. NIGHTWATCH.[6]
- SCHOOLMONTANA: Software that makes DNT implants persistent on JUNOS-based (FreeBSD-variant) J-series routers/firewalls.[22]
- SIERRAMONTANA: Software that makes DNT implants persistent on JUNOS-based M-series routers/firewalls.[22]
- STUCCOMONTANA: Software that makes DNT implants persistent on JUNOS-based T-series routers/firewalls.[22]
- SOMBERKNAVE: Software that can be implanted on a Windows XP system allowing it to be remotely controlled from NSA headquarters.
- SOUFFLETROUGH: BIOS injection software that can compromise Juniper Networks SSG300 and SSG500 series firewalls.[22]
- SPARROW II

- SPARROW II: (see image at right) A small computer intended to be used for WLAN collection, including from UAVs. Hardware: IBM Power PC 405GPR processor, 64 MB SDRAM, 16 MB of built-inflash, 4 mini PCI slots, CompactFlash slot, and 802.11 B/G hardware. Running Linux 2.4 and the BLINDDATE software suite. Unit price (2008): $6K.
- SURLYSPAWN: Keystroke monitor technology that can be used on remote computers that are not internet connected.
- SWAP: Technology that can reflash the BIOS of multiprocessor systems that run FreeBSD, Linux, Solaris, or Windows.
- TAWDRYYARD

- TOTECHASER

- TOTEGHOSTLY: Software that can be implanted on a Windows mobile phone allowing full remote control.
- TRINITY: (see image at right) A more recent and more powerful multi-chip module using a 180 MHz ARM9 processor, 4 MB of flash, 96 MB of SDRAM, and a FPGA with 1 million gates. Smaller than a penny. Estimated cost (2008) $625K for 100 units.
- WATERWITCH: A portable "finishing tool" that allows the operator to find the precise location of a nearby mobile phones.
- WISTFULTOLL

---
List of XKEYSCORE fingerprints:With XKeyscore, his staff discovered "new traffic and documents," raves a
unit manager in the Africa department. Among the catch, the unit
manager notes according to the document, was material from the Tunisian
Interior Ministry that no other surveillance system had managed to
capture.
https://fveydocs.org/blog/xks-fingerprints/
The Digital Arms Race: NSA Preps America for Future Battle
https://fveydocs.org/document/making-passive-sexy/
The US intelligence service codename for the bugging operation targeting the EU mission at the United Nations is "Perdido".
The operation against the French mission to the UN had the covername "Blackfoot" and the one against its embassy in Washington was "Wabash". The Italian embassy in Washington was known to the NSA as both "Bruneau" and "Hemlock".
The eavesdropping of the Greek UN mission was known as "Powell" and the operation against its embassy was referred to as "Klondyke".
https://web.archive.org/web/20141229010849/http://www.theguardian.com/world/2013/jun/30/nsa-leaks-us-bugging-european-allies

The so-called "Dagger Complex" is one of the best protected sites in the German state of Hesse.
agency's European Cryptologic Center (ECC) is headquartered in
Griesheim. A 2011 NSA report indicates that the ECC is responsible for
the "largest analysis and productivity in Europe."
https://web.archive.org/web/20141231025458/http://www.spiegel.de/international/world/germany-is-a-both-a-partner-to-and-a-target-of-nsa-surveillance-a-916029.html
-----Comments:
"Although this article asserts that the US is spying on Germany, all the details suggest that the BND is spying on Germans and sharing information with the US (Obama's desk). You report that the US spying is focused on larger terrorist operations and not trade and that the BND knows about it. In fact, the NSA has cultivated a relationship of equals with the BND and taught them to use its most secret, most advanced intelligence tools. It sounds like Germans have a problem with their own government, not the dreaded Anglo-Saxon menace."
"The NSA has been intercepting and analyzing the entire electromagnetic spectrum since 1987 using multiple Tektronix 3052 realtime spectrun analyzers to capture signals for analysis by its supercomputers. This is non confidential information because NSA used commercially available off the shelf (COTS) equipment operated with instructions published by Tektronix. The Tektronix 3052 instrument achieved ‘First Prize for Best Technology, WesCon 1988’. Its not a secret. It never was. The change from analog to digital communications since 1987 just makes interception that much simpler. However the interception and transmission of data over government owned or controlled lines from the tap to the analysis system is a warrantless wiretap by definition. Seizing and searching the haystack to find the needle is unconstitutional. By selfishly failing to warn Americans that this capability exists, the entire internet/cellular communication system is vulnerable to surveillance by hostile forces. The arrogance of the NSA is beyond belief. Do they think that the Chinese, Russians and Indians are stupid? In fact, the 3052 was designed by a polyglot mixture of Vietnamese, Indian, Chinese, Egyptian & American born engineers. I was one of the Americans. The failure to provide encryption of all conversations, emails, etc. has left the entire internet vulnerable to a cyber Pearl Harbor. Does NSA think that their software backdoors can’t be opened by reverse engineering? Or their viruses reverse engineered and “improved”? At the very least Generals Hayden, Alexander et al should be prosecuted and imprisoned on an Unlawful Search & Seizure theory. When characterizing Stalin, the Russian Marxist Nikolai Bukharin also described the NSA perfectly as being “an infernal machine that seems to use medieval methods, yet possesses gigantic power, fabricates organized slander, acts boldly and confidently…” NSA can keep their spy network, Americans need to demand encrypted communications before an “improved” Stuxnet virus launches into a US nuclear power plant."
"At the end of WW II USA was the last man standing, I mean the only industrialized country with its infrastructure intact (Churchill Jacobson said that UK won the war but the British Emporium was completely lost in the next 5 years...). In 2013 USA’s competitive advantage has vanished and simply cannot compete with nations with large populations like China or even India that are quickly ereducing the technological gap of the XIX and XX centuries…. Today, size matters as well as talent and high-tech, a German leading edge since, lest we forget, man reached the moon thanks to Werner Von Braun…"
"The internet was intended to be a weapon to be used after a nuclear attack destroying centralized communications, and it remains so, a US controlled weapon up until the free world takes over or duplicates it…."
"Peter Wright wrote about bugging a French encrypted telex line at the London embassy by picking up the "ghost" signal that leaked out, and that was back in the 1950s."
"All the major news channels are owned by corporate America. The same corporate America that also owns the politicians.
Here are a couple of books worth reading: Legacy of Ashes, The history of the CIA, and Enemies, A history of the FBI. Both were written by Tim Weiner. Enjoy.
Don't expect the truth to come to you. You have to seek it out.
Don't expect your politicians to tell the truth. In many cases they don't know what the truth may be and are unlikely to seek it out as they are too busy"
"Are we surprised that paedophile rings operate around the globe? No.
Does that sanction their behaviour? No."
"Are the US and UK Governments aware of all of the Guardian's evidence or are they only informed as the paper plans to release each story?"
"The Guardian may warm governments the night it goes to press, but I wouldn't think so in this case"
"Rushbridger said in an interview they show the leaked material they are planning to print and ask if there is a specific security reason why they shouldn't publish.
As for the extent of the leaks, I'm assuming Booz Allen was able to
tell the government what Snowden had access to. He probably copied just
about anything incriminating he could lay his hands on."
"They must certainly know how much information Snowden had access to and was able to extract. So I'd guess they already know what he knows..."
"they own internet services and hardware that everyone - the world over, uses - which is American designed and thus susceptible to US State and NSA surveillance.
That is the main issue here, everything internet and comms related has been Americanised, to the companies the world uses and the hardware. It has left everyone, every company and every state that is non American vulnerable."
"'Insider Threat: Government Employees Urged to Tattle On Coworkers in Effort to Stop Classified Leaks'.
This also involves government employees who have no connection to intelligence agencies. For example those include people working in the peace core, the department of social security administration, department of education, agriculture and so on.
http://www.democracynow.org/2013/6/25/insider_threat_government_employees_urged_to
Also look at this
http://finance.yahoo.com/news/original-nsa-whistleblower-know-nsa-143100665.html "
"Actually, it was CERN and Sir Tim Berners-Lee's team there who invented the WWW... I don't think CERN spies on the US, does it?"
"Nevertheless, whilst non US consumers and the masses will continue to use Facebook, Google, Microsoft, Yahoo and Apple, many non American companies and of course states are, as you eloquently put it, "getting the fuck out"..... if anything this debacle has shown not even private American companies and businesses can be trusted - therefore surely now European, African, South American and Asian nations and companies must be creating their own internet platforms and hardware, to erode that dependence on American tech and comms."
"Now lets see William Hague tell the EU how all of this is legal, and "If you've got nothing to hide, you've got nothing to worry about"...
And hey, i really do like, to keep information saved, that can be used, for good. Margus Meigo"They must certainly know how much information Snowden had access to and was able to extract. So I'd guess they already know what he knows..."
"they own internet services and hardware that everyone - the world over, uses - which is American designed and thus susceptible to US State and NSA surveillance.
That is the main issue here, everything internet and comms related has been Americanised, to the companies the world uses and the hardware. It has left everyone, every company and every state that is non American vulnerable."
"'Insider Threat: Government Employees Urged to Tattle On Coworkers in Effort to Stop Classified Leaks'.
This also involves government employees who have no connection to intelligence agencies. For example those include people working in the peace core, the department of social security administration, department of education, agriculture and so on.
http://www.democracynow.org/2013/6/25/insider_threat_government_employees_urged_to
Also look at this
http://finance.yahoo.com/news/original-nsa-whistleblower-know-nsa-143100665.html "
"Actually, it was CERN and Sir Tim Berners-Lee's team there who invented the WWW... I don't think CERN spies on the US, does it?"
"Nevertheless, whilst non US consumers and the masses will continue to use Facebook, Google, Microsoft, Yahoo and Apple, many non American companies and of course states are, as you eloquently put it, "getting the fuck out"..... if anything this debacle has shown not even private American companies and businesses can be trusted - therefore surely now European, African, South American and Asian nations and companies must be creating their own internet platforms and hardware, to erode that dependence on American tech and comms."
"Now lets see William Hague tell the EU how all of this is legal, and "If you've got nothing to hide, you've got nothing to worry about"...
They've been awfully quiet, haven't they? I didn't see Sunday Politics on the BBC today, was the subject at all mentioned?"
"
Stealing; 1. To take (the property of another) without right or permission.
2. To present or use (someone else's words or ideas) as one's own.
3. To get or take secretly or artfully: steal a look at a diary; steal the puck from an opponent.
4. To give or enjoy (a kiss) that is unexpected or unnoticed.
5. To draw attention unexpectedly in (an entertainment), especially by being the outstanding performer: The magician's assistant stole the show with her comic antics.
6. Baseball To advance safely to (another base) during the delivery of a pitch, without the aid of a base hit, walk, passed ball, or wild pitch.
v.intr.
Now how can we steal something back from that country of freedom, religios nucases and lest we forget land of the just?"
"Not quite. The rest of the EU (i.e. most of it) should throw Britain out, and leave NATO (except for the ones already sensible enough not to be in it)." (2013)
"It feels like it is only the Guardian pushing this story hard.
Anyone know why other publications or broadcasters seem to consider it not top news?
It seems peculiar, no?"
"I believe Snowden released the data to the Guardian and The Washington Post. Other newspapers don't have access to it, as far as I know."
Benjine"Because it IS a non story. I've been asking for over a week for somebody to come forward and tell me something bad that has happened to them in their actual lives - rather than the ones they imagine themselves leading - and so far nobody...not a single Guardian reader...can actually detail anything bad that has happened to theme personally as a result of the PRISM program."
"I'm sure there are many horrible things that have happened throughout history that have had no effect on your life."
"Nail on the Head , too many people read 1984 as kids and decided it was 100% based on fact in the uk.
"The PRISM program is only a label. Blanket surveillance is the issue.
"The Guardian is owned by a Trust with no shareholders. The government doesn't censor comments on CiF but they may be removed if they are libellous to protect the newspaper from being sued. That is civil law and under review after a civil society campaign."
"The Guardian is notorious for breaking the news that the majority of people don't want to take in as they'd rather keep their heads buried etc. If there's a story with a big revelation, which has huge implications - the guardian will print it, because that's what their readership wants. They want the hard shit."
"Michael Hastings, contributing editor for Rolling Stone magazine, and famous for reporting General McCrystal's contempt for Obama, which lead to McCrystal being fired, published a book called The Operators: the Wild and Terrifying Inside Story of America's War in Afghanistan, in which he says:
"
Stealing; 1. To take (the property of another) without right or permission.
2. To present or use (someone else's words or ideas) as one's own.
3. To get or take secretly or artfully: steal a look at a diary; steal the puck from an opponent.
4. To give or enjoy (a kiss) that is unexpected or unnoticed.
5. To draw attention unexpectedly in (an entertainment), especially by being the outstanding performer: The magician's assistant stole the show with her comic antics.
6. Baseball To advance safely to (another base) during the delivery of a pitch, without the aid of a base hit, walk, passed ball, or wild pitch.
v.intr.
Now how can we steal something back from that country of freedom, religios nucases and lest we forget land of the just?"
"Not quite. The rest of the EU (i.e. most of it) should throw Britain out, and leave NATO (except for the ones already sensible enough not to be in it)." (2013)
"It feels like it is only the Guardian pushing this story hard.
Anyone know why other publications or broadcasters seem to consider it not top news?
It seems peculiar, no?"
"I believe Snowden released the data to the Guardian and The Washington Post. Other newspapers don't have access to it, as far as I know."
Benjine"Because it IS a non story. I've been asking for over a week for somebody to come forward and tell me something bad that has happened to them in their actual lives - rather than the ones they imagine themselves leading - and so far nobody...not a single Guardian reader...can actually detail anything bad that has happened to theme personally as a result of the PRISM program."
"I'm sure there are many horrible things that have happened throughout history that have had no effect on your life."
"Nail on the Head , too many people read 1984 as kids and decided it was 100% based on fact in the uk.
The guardian has become the first place to come for David Icke fans."
"The PRISM program is only a label. Blanket surveillance is the issue.
I seem to remember replying to one of your posts on another thread
with the example of how the security forces leaked data that ended up on
UK construction worker blacklists; the effect of which was to destroy
many people's lives. This is a perfect example of how state agencies can
abuse access to private data and how it most definitely does harm
ordinary people."
"Benjine, I believe you have missed out on
quite a bit of news while you've been hiding in that cave of yours, so
here's a refresher from Sibel Edmonds, William Binney, Russell Tice and
Glenn Greenwald, et al.
http://www.youtube.com/watch?list=UU7TvL4GlQyMBLlUsTrN_C4Q&v=Pc3esnkqM7E&feature=player_embedded
http://www.counterpunch.org/2013/06/26/why-the-ruling-class-is-so-upset-about-edward-snowden/
http://www.youtube.com/watch?v=hfS2Op9l3nk
http://www.youtube.com/watch?v=TuET0kpHoyM
http://www.youtube.com/watch?v=CPyxeqcCjkc
http://www.youtube.com/watch?v=pfXxl0PX__g
And Glenn,
https://www.youtube.com/watch?feature=player_embedded&v=Uulv4ve6RJ8 "
http://www.counterpunch.org/2013/06/26/why-the-ruling-class-is-so-upset-about-edward-snowden/
http://www.youtube.com/watch?v=hfS2Op9l3nk
http://www.youtube.com/watch?v=TuET0kpHoyM
http://www.youtube.com/watch?v=CPyxeqcCjkc
http://www.youtube.com/watch?v=pfXxl0PX__g
And Glenn,
https://www.youtube.com/watch?feature=player_embedded&v=Uulv4ve6RJ8 "
"The Guardian is owned by a Trust with no shareholders. The government doesn't censor comments on CiF but they may be removed if they are libellous to protect the newspaper from being sued. That is civil law and under review after a civil society campaign."
"The Guardian is notorious for breaking the news that the majority of people don't want to take in as they'd rather keep their heads buried etc. If there's a story with a big revelation, which has huge implications - the guardian will print it, because that's what their readership wants. They want the hard shit."
"Michael Hastings, contributing editor for Rolling Stone magazine, and famous for reporting General McCrystal's contempt for Obama, which lead to McCrystal being fired, published a book called The Operators: the Wild and Terrifying Inside Story of America's War in Afghanistan, in which he says:
- the Pentagon now spends the staggering amount of $4.7 billion a year on 27,000 public-relations people
- the Pentagon is the largest employer in the US - employing 3.3 million people
- 54% of US federal tax dollars goes to the Pentagon
- The Pentagon has 17 different intelligence agencies
- Many foreign correspondents are thinly disguised propaganda agents
"This is a huge, huge operation," Hastings says, "And one of the main goals the Pentagon has set out is to win the global information war."
Many are also employed as sock puppets to derail online conversations sympathetic to the Left.
The founding fathers of the US recognised that the military posed a threat to civil society and attempted to limit their control within the Constitution. After WW2, however, there was an expansion of this permanent national security state so that it is now 'probably the most powerful institution in Washington.'
Any wonder, then, that every man, woman child and cat in the world is under surveillance? Clearly they have to justify their existence somehow because the alternative is possibly the unemployment queue.
"What we are doing is not making the world safer," Hastings says.
"Peculiar? I'd say expected. The other media are worthless hypocrites. There are some good ones besides Glenn, like Rolling Stones writer Matt Taibbi, who recently took on New York Times Dealbook writer Andrew Ross Sorkin for his stupid remarks about Glenn Greenwald and called Sorkin "a shameless, ball-gargling prostitute for Wall Street?"
- the Pentagon is the largest employer in the US - employing 3.3 million people
- 54% of US federal tax dollars goes to the Pentagon
- The Pentagon has 17 different intelligence agencies
- Many foreign correspondents are thinly disguised propaganda agents
"This is a huge, huge operation," Hastings says, "And one of the main goals the Pentagon has set out is to win the global information war."
Many are also employed as sock puppets to derail online conversations sympathetic to the Left.
The founding fathers of the US recognised that the military posed a threat to civil society and attempted to limit their control within the Constitution. After WW2, however, there was an expansion of this permanent national security state so that it is now 'probably the most powerful institution in Washington.'
Any wonder, then, that every man, woman child and cat in the world is under surveillance? Clearly they have to justify their existence somehow because the alternative is possibly the unemployment queue.
"What we are doing is not making the world safer," Hastings says.
"Peculiar? I'd say expected. The other media are worthless hypocrites. There are some good ones besides Glenn, like Rolling Stones writer Matt Taibbi, who recently took on New York Times Dealbook writer Andrew Ross Sorkin for his stupid remarks about Glenn Greenwald and called Sorkin "a shameless, ball-gargling prostitute for Wall Street?"
Nobody has ever described Sorkin better - the description should be
carved on his tombstone. Thanks, Matt, and Glenn and Snowden and Manning
and Assange.
Read more: http://www.rollingstone.com/politics/blogs/taibblog "
"What about asking one out of the 80000 people a year who are stunned when they access their Stasi files and find out that close friends weren't friends but spies?
The Stasi tapped 40 calls a day in the DDR. The NSA taps 20 million(!) connections per day in Germany.
A non-story. For sure.."
" Your comments make perfect sense as long as we simply assume that our governments always necessarily have all our best interests at heart. It seems from your 'keeping us safe during the Cold War' comment that you're quite happy to assume this.
Read more: http://www.rollingstone.com/politics/blogs/taibblog "
"What about asking one out of the 80000 people a year who are stunned when they access their Stasi files and find out that close friends weren't friends but spies?
The Stasi tapped 40 calls a day in the DDR. The NSA taps 20 million(!) connections per day in Germany.
A non-story. For sure.."
" Your comments make perfect sense as long as we simply assume that our governments always necessarily have all our best interests at heart. It seems from your 'keeping us safe during the Cold War' comment that you're quite happy to assume this.
However, if we assume this, what's wrong with China's approach to
internet censorship? After all, they've only got the Chinese people's
best interests at heart, right? A lot of Chinese people agree with this
idea.
What was wrong with Stalin or Hitler's internal security policies? After all, they wouldn't have done what they did if it wasn't really in their people's best interests, would they? A lot of Soviet/German people agreed with this idea.
Did it never occur to you that Western governments wanted to keep 'us' safe during the Cold War not because they really cared about each and every last one of us but because they wanted to preserve their systems of privilege and power? And the same for the Soviet government, of course, just like the Chinese government today.
There's a reason why people like Orwell were so concerned about 'Big Brother' surveillance systems: once a government (or any other group or individual) has this much power, they (or some part of them) will at some point inevitably misuse it for their own purposes, the consequences for the nation and its people being far worse than any individual acts of terrorism.
The same is equally true for military power: once the US military developed the point of being far more powerful than any other, it was only a matter of time before this was misused to expand US control of resources as in Iraq/etc. "
What was wrong with Stalin or Hitler's internal security policies? After all, they wouldn't have done what they did if it wasn't really in their people's best interests, would they? A lot of Soviet/German people agreed with this idea.
Did it never occur to you that Western governments wanted to keep 'us' safe during the Cold War not because they really cared about each and every last one of us but because they wanted to preserve their systems of privilege and power? And the same for the Soviet government, of course, just like the Chinese government today.
There's a reason why people like Orwell were so concerned about 'Big Brother' surveillance systems: once a government (or any other group or individual) has this much power, they (or some part of them) will at some point inevitably misuse it for their own purposes, the consequences for the nation and its people being far worse than any individual acts of terrorism.
The same is equally true for military power: once the US military developed the point of being far more powerful than any other, it was only a matter of time before this was misused to expand US control of resources as in Iraq/etc. "
It IS a story, and it is also in this morning's Le Figaro, here in Paris:
http://www.lefigaro.fr/international/2013/06/30/01003-20130630ARTFIG00177-espionnage-americain-les-europeens-reclament-des-comptes-aux-etats-unis.phps
http://www.lefigaro.fr/international/2013/06/30/01003-20130630ARTFIG00177-espionnage-americain-les-europeens-reclament-des-comptes-aux-etats-unis.phps
"This is kind of a silly idea, and also the kind the power structure
loves. It does not take a genius, nor does it take immediately present
and available evidence to know, simply from the shear volume of data
being collected, that regardless of the fact that no one is available
this instant to answer your childish call for evidence of harm, that
both the hazard and the likelihood of abuse and harm do indeed exist,
and will indeed manifest themselves in time, by which time it will be
too late to do anything about it.
It works like this: the information is stored, and when needed, it will be called up. It need never even show up in a court, but it will definitely be used by the power structure to the denigration of the target.
The irony of it is that it silences people preemptively, because PRISM knows their secrets, even the kind which are no breach of any law, even it's not yet read them, they know these secrets are likely already in possession of those in a position to cause them harm. So sure, they don't say a thing, and you may never SEE the concrete evidence of harm for which you pine, but that is only because the harm is the invisible kind: the chilling and the freezing of speech never uttered, the silencing of dissent without any gun."
Benjine "
"One of documents Snowden handed to Der Spiegl we get actual figures for Germany. On one "high traffic" day, namely January 7 2013, the NSA intercepted and listened in on/recorded 60 million phone calls! 60 million phone calls in one country in one day! It's mind-boggling!"
"
It works like this: the information is stored, and when needed, it will be called up. It need never even show up in a court, but it will definitely be used by the power structure to the denigration of the target.
The irony of it is that it silences people preemptively, because PRISM knows their secrets, even the kind which are no breach of any law, even it's not yet read them, they know these secrets are likely already in possession of those in a position to cause them harm. So sure, they don't say a thing, and you may never SEE the concrete evidence of harm for which you pine, but that is only because the harm is the invisible kind: the chilling and the freezing of speech never uttered, the silencing of dissent without any gun."
Benjine "
Too many fires to fight and I have work
to get on with - nothing to do with my night time work trolling for the
NSA understand ;) !!
But I wanted just to say a couple of things in relation to your post;
A couple of points in relation to that;
First, I remember in the immediate aftermath of 9/11 every man and his dog in the media was saying "we need to have better human intelligence".
Second, the Iraq War was, above all, a failure of intelligence (and then imagination). Our issue viz Iraq wasn't relating to defence intel or signals intel it was to do with our lack of people on the ground, in Saddamite Iraq who actually knew what was going on. I seem to remember we ended up relying on a highly dubious figure called Ahmed Chalabi who hadn't even lived in the country for many years but who, we were assured, had "friends" in Iraq.
So more, better, human intelligence was needed to prevent the kinds of catastrophic failures of 9/11 & the war in Iraq. And yet what happened? Well, in part we don't know. Or we don't know details. And that's as it should be.
I can speculate that budgets in this area (humint) have been expanded dramatically since 01. But here's the difference between me and most in here. I don't need or want to know how the intel community spends its budget. Its the only bit of government that I need take no interest in. In some ways its the only bit of government I do trust. So yes, for some reason I do trust the spooks. And I know that most here don't. Which makes for a difficult debate.
I don't know how inaccurate it is ... i trust you do? I also didn't know that it was a consequence of "sifting inaccurate data" that led to the drone attacks on those wedding parties in 2008 - appalling as they were? Can you verify for me?
I also don't know the veracity of the 2nd claim regarding unlawful imprisonment, rendition.
If its worthless as intelligence - like waterboarding - then I don't know why they go in for it. But I'm not in favour of waterboarding in spite of what you might think! "
"
"Oh just stop with this ridiculous nonsense already please Guardian. Your reports today already indicate at your focus on this total non issue is having deleterious impact on international relations and is potentially damaging the posssibiltiy of a breakthrough in the VITAL EU-USA trade agreement on which potentially hundreds of thousands of jobs depend.
But I wanted just to say a couple of things in relation to your post;
yet the agencies are so enamoured of the big budget hi-tech approach they have neglected on the ground humint for far too longThis is actually the smartest thing I've read in here on this issue for a while and certainly one that should be a priority... the balance between Sigint - what everyone's worked up about - and Humint... something that people feel pretty relaxed about I would hope / guess.
A couple of points in relation to that;
First, I remember in the immediate aftermath of 9/11 every man and his dog in the media was saying "we need to have better human intelligence".
Second, the Iraq War was, above all, a failure of intelligence (and then imagination). Our issue viz Iraq wasn't relating to defence intel or signals intel it was to do with our lack of people on the ground, in Saddamite Iraq who actually knew what was going on. I seem to remember we ended up relying on a highly dubious figure called Ahmed Chalabi who hadn't even lived in the country for many years but who, we were assured, had "friends" in Iraq.
So more, better, human intelligence was needed to prevent the kinds of catastrophic failures of 9/11 & the war in Iraq. And yet what happened? Well, in part we don't know. Or we don't know details. And that's as it should be.
I can speculate that budgets in this area (humint) have been expanded dramatically since 01. But here's the difference between me and most in here. I don't need or want to know how the intel community spends its budget. Its the only bit of government that I need take no interest in. In some ways its the only bit of government I do trust. So yes, for some reason I do trust the spooks. And I know that most here don't. Which makes for a difficult debate.
You clearly have no idea of how inaccurate 'sifting' is and how it leads to drones attacking and wiping out wedding parties (for example) because the 'metadata' showed a 'threat'. This is the same data from sifting that has been used to kidnap people and incarcerate them in secret prisons. The level of material extracted by analysis at this level is completely worthless as intelligence.That is true.
I don't know how inaccurate it is ... i trust you do? I also didn't know that it was a consequence of "sifting inaccurate data" that led to the drone attacks on those wedding parties in 2008 - appalling as they were? Can you verify for me?
I also don't know the veracity of the 2nd claim regarding unlawful imprisonment, rendition.
If its worthless as intelligence - like waterboarding - then I don't know why they go in for it. But I'm not in favour of waterboarding in spite of what you might think! "
"
Bullshit.
Suggest you Google the following: 'Maher Ara'r and 'Khalid El-Masri'.
Nothing to hide, nothing to fear. Lol. "
"
If you are an unrepentant 'nonconformist' in your lifestyle choices as defined by the powers-that-be then you have something to worry about. That would be me. If you are an individual with passionate political beliefs that are considered 'threatening' by the powers-that-be and you communicate those beliefs in any way open to this unseen scrutiny, you have something to worry about. That would be me. If you are an individual with high integrity, a highly developed sense of what is ethical and moral and the courage to act in accordance with your beliefs then you have something to worry about. That would be me.
If, like me, you flirted with alternative ideologies as a student in the 1970s and personally knew others more outspoken and more pro-active in communicating their ideas who found their names on various lists compiled by interested agencies and were sometimes therefore ostracised, harrassed or arrested because of that, then you would have something to worry about.
If, like me, you have (recently) been the victim of cowardly liars hiding behind a public facade of designated authority and respectability and found that the legal/justice system is finely tuned to protect those with money and power from the unwanted attentions of uppity individuals, then you would have something to worry about.
People who find themselves in positions of power and control strive to retain it. One way to do this is to eliminate all opposition. The possibility of blanket surveillance of a populace in order to assist achieving this is a powerful tool. I have absolutely no faith that the current power elites anywhere can be trusted to use such a tool ethically and humanely.
Suggest you Google the following: 'Maher Ara'r and 'Khalid El-Masri'.
Nothing to hide, nothing to fear. Lol. "
"
If you are an unrepentant 'nonconformist' in your lifestyle choices as defined by the powers-that-be then you have something to worry about. That would be me. If you are an individual with passionate political beliefs that are considered 'threatening' by the powers-that-be and you communicate those beliefs in any way open to this unseen scrutiny, you have something to worry about. That would be me. If you are an individual with high integrity, a highly developed sense of what is ethical and moral and the courage to act in accordance with your beliefs then you have something to worry about. That would be me.
If, like me, you flirted with alternative ideologies as a student in the 1970s and personally knew others more outspoken and more pro-active in communicating their ideas who found their names on various lists compiled by interested agencies and were sometimes therefore ostracised, harrassed or arrested because of that, then you would have something to worry about.
If, like me, you have (recently) been the victim of cowardly liars hiding behind a public facade of designated authority and respectability and found that the legal/justice system is finely tuned to protect those with money and power from the unwanted attentions of uppity individuals, then you would have something to worry about.
People who find themselves in positions of power and control strive to retain it. One way to do this is to eliminate all opposition. The possibility of blanket surveillance of a populace in order to assist achieving this is a powerful tool. I have absolutely no faith that the current power elites anywhere can be trusted to use such a tool ethically and humanely.
but it actually IS true that if you have nothing to hide you have absolutely nothing to fear.Who defines whether you have nothing to hide? I am astonished at your naivety "
"Oh just stop with this ridiculous nonsense already please Guardian. Your reports today already indicate at your focus on this total non issue is having deleterious impact on international relations and is potentially damaging the posssibiltiy of a breakthrough in the VITAL EU-USA trade agreement on which potentially hundreds of thousands of jobs depend.
I thought Guardian readers were in favour of more jobs? Less unemployment? "
You do know that this latest "trade"
agreement will mostly benefit corporations, right? They will get to sue
governments trying to regulate them, and Wall Street banksters will get
even less constraints the next time they wreck European economies.
Actual trade of goods and useful services is already free enough between the US and the EU.
As for the "hundreds of thousands of jobs", that's neoliberal propaganda. How did the last few trade treaties work out for that?
As for the "hundreds of thousands of jobs", that's neoliberal propaganda. How did the last few trade treaties work out for that?
""Trade" agreements are rarely about trade or jobs. They're usually about subverting the democratic process.
To the extent trade deals have economic goals, trade deals negotiated
behind closed doors are about maximizing profit, usually involving the
elimination (not creation) of hundreds of thousands of jobs."
"One of documents Snowden handed to Der Spiegl we get actual figures for Germany. On one "high traffic" day, namely January 7 2013, the NSA intercepted and listened in on/recorded 60 million phone calls! 60 million phone calls in one country in one day! It's mind-boggling!"
"
The information that is being collected
is a detailed analysis of how individuals interact with each other - en
masse this provides information regarding how society works on a
fundamental level. Society is essentially communication and interaction.
Combined with an understanding of how to influence individuals (advertising has spent billions understanding how humans think) the people controlling this information will be able to influence society.
They can push society in the direction they wish us to go - one can assume this means more individual, less politically active or community minded, more likely to accept low pay and expensive goods/housing, lower education standards focusing on 'learning by rote' rather than dangerous 'free thinking' and more distracted by cheap entertainment.
Will we know they've done it? No. How could we? It's an incremental, slow and insidious project. Without people like Snowden it would be a complete secret.
To believe that the US (and UK) intelligence agencies have happily ignored morality/privacy/trust when collecting all this information, notably spying on their own citizens and other friendly countries, but that they would stop short of using it to its full immoral potential is just a little bit strange.
Why do you think they would draw the line just short of influencing their own citizens when they ignored the line that marked out privacy and other legal rights?
And if the US/UK intelligence agencies are really doing all of this for the good of us all - protecting us from potential terrorists etc. Then they are doing it for a reason that kills less people than bath tub falls and the killings carried out by the police.
Again, a little strange that citizens have to lose their rights for such a small number of deaths. "
"Too bad Hastings is dead. He died recently in an unexplained high-speed car crash. He was working on what he called a big story on national security issues that would "blow [people's] minds". The day that he died he said that he was being investigated by "the feds". There's no evidence of foul play in the accident, but who can claim that large-scale surveillance doesn't have a corrosive effect on society?
Combined with an understanding of how to influence individuals (advertising has spent billions understanding how humans think) the people controlling this information will be able to influence society.
They can push society in the direction they wish us to go - one can assume this means more individual, less politically active or community minded, more likely to accept low pay and expensive goods/housing, lower education standards focusing on 'learning by rote' rather than dangerous 'free thinking' and more distracted by cheap entertainment.
Will we know they've done it? No. How could we? It's an incremental, slow and insidious project. Without people like Snowden it would be a complete secret.
To believe that the US (and UK) intelligence agencies have happily ignored morality/privacy/trust when collecting all this information, notably spying on their own citizens and other friendly countries, but that they would stop short of using it to its full immoral potential is just a little bit strange.
Why do you think they would draw the line just short of influencing their own citizens when they ignored the line that marked out privacy and other legal rights?
And if the US/UK intelligence agencies are really doing all of this for the good of us all - protecting us from potential terrorists etc. Then they are doing it for a reason that kills less people than bath tub falls and the killings carried out by the police.
Again, a little strange that citizens have to lose their rights for such a small number of deaths. "
"Too bad Hastings is dead. He died recently in an unexplained high-speed car crash. He was working on what he called a big story on national security issues that would "blow [people's] minds". The day that he died he said that he was being investigated by "the feds". There's no evidence of foul play in the accident, but who can claim that large-scale surveillance doesn't have a corrosive effect on society?
Conspiracy theorists looking to be entertained, and anyone wanting to
feel very very very scared and paranoid, and anyone looking to buy a
new car, should look here. (By the way, I think the accident was probably just an accident, but there's no way to be certain).
My point is that no investigative journalist -- or anyone else -- should be made to feel paranoid. If somoeone can get charged with espionage for revealing government misconduct, and the government has unlimited surveillance powers to catch "spies", democracy is finished. "
"Europe seems to be pissed that the Anglosphere is better at this game than they are.
"Up until now there has been little coverage in France. This has changed dramatically today. Every newspaper and TV station is talking about events now. Some are saying that political talk with the US Stasi is out of the question now and more to the point, legal action should be taken against them. Others who are equally outraged are demanding for the Statue of Liberty to be returned. How things have changed!
"The extent of your delusion is incredible. Are you seriously saying that other countries don't have spy networks? Tow the statue of liberty away by all means but put it where exactly? In one of the countries that do exactly the same as the US but if a Snowden came forward from those countries he would be dining on some radioactive sushi very quickly?"
"Least we forget MARKSTALLARD the result of the forensic examination of the corpse of the Palestine leader, Arafat, also seem to be a little overdue ? Talking about exotic foodstuffs, you understand."
https://en.wikipedia.org/wiki/Censorship_by_country
https://en.wikipedia.org/wiki/Internet_censorship_and_surveillance_by_country
My point is that no investigative journalist -- or anyone else -- should be made to feel paranoid. If somoeone can get charged with espionage for revealing government misconduct, and the government has unlimited surveillance powers to catch "spies", democracy is finished. "
"Europe seems to be pissed that the Anglosphere is better at this game than they are.
I'd take the Anglosphere's pluck and espionage ingenuity over Europe's history of communist and fascist totalitarianism any day."
"
"According to an earlier Glenn Greenwald article, they are recording the contents (not just the metadata) of both emails and phone calls""
For those who didn't click
Inverted totalitarianism. It is all politics all of the time but a politics largely untempered by the political. Party squabbles are occasionally on public display, and there is a frantic and continuous politics among factions of the party, interest groups, competing corporate powers, and rival media concerns. And there is, of course, the culminating moment of national elections when the attention of the nation is required to make a choice of personalities rather than a choice between alternatives. What is absent is the political, the commitment to finding where the common good lies amidst the welter of well-financed, highly organized, single-minded interests rabidly seeking governmental favors and overwhelming the practices of representative government and public administration by a sea of cash
"
Inverted totalitarianism. It is all politics all of the time but a politics largely untempered by the political. Party squabbles are occasionally on public display, and there is a frantic and continuous politics among factions of the party, interest groups, competing corporate powers, and rival media concerns. And there is, of course, the culminating moment of national elections when the attention of the nation is required to make a choice of personalities rather than a choice between alternatives. What is absent is the political, the commitment to finding where the common good lies amidst the welter of well-financed, highly organized, single-minded interests rabidly seeking governmental favors and overwhelming the practices of representative government and public administration by a sea of cash
"
"Actually Latin America has a worse history in all of those regards than
the USA has. The vast majority of slavery occurred in Latin America and
the Carribean, not the US. and The US has a far better record when it
comes to treatment of Native Americans than do Latin American countries."
"
Read up about the "Trail of Tears" and you will HOPEFULLY retract that statement...
"
"
"If you visit Mexico City, you can meet a lot of Aztecs. If you go to
Cuzco, you can meet a lot of Incas. Go to Boston, and you will not meet a
lot of Pequods. Go to NYC and you will not meet a lot of Manhattans. Go
to DC and you will not meet a lot of Powhatans "
"
Yes, it's clearly only those dodgy
Europeans who are susceptible to fascism. The US obviously wouldn't ever
go down that route, lacking things like excessive nationalism
indoctrinated through the education system, exceptionalism and the view
that one's own country is somehow different or special, a bloated and
excessive military engaged in aggressive wars for resources, a
sophisticated surveillance system to keep track of dissidents, a
political system completely intertwined with corporate interests, a
suspicion of anything 'foreign', a supine media controlled by the same
interests who run government and corporations, mindless entertainment to
distract the masses from their real economic and political situation,
control and monitoring of unions and grassroots organizations, the view
that to criticise one's own country is unpatriotic...
No, clearly Frank Zappa was right in 1966, it can't happen here." (irony)
No, clearly Frank Zappa was right in 1966, it can't happen here." (irony)
"Actually the Washington Post is helping blow around the "hot air"
(something that wasn't even technically feasible until recently –
machine learning algorithms sorting through data on relatively cheap
storage space via the digitization of all media – yes, all technologies
are equivalent, you sound like you know what you're talking about, and
"hot air" is not also what blows outside in the summer) around again
with a new set of slides."
"You and all the complacent sheep have little to worry about, for now.
We political dissidents, however, do mind if a vast surveillance state
is reading our emails.
The FBI labeled Occupy a "domestic terrorist threat," and infiltrated it and sought to subvert it. Police brutality became a hallmark of the government's response to that movement. I'm sure the NSA is intercepting activists' emails, and reading them.
People like you are the last to come into the state's sights. But when you do, you'll click your heels and thank the authorities for hanging you."
// it was actually...
"U.S. is actually amassing troops in Australia as part of Obama's "piivot to Asia", and because Russia and China do not support the attempted U.S. coup in Syria, these are serious ramifications indeed. World War III is a bit more serious than temporary annoyance or embarrassment."
"No other country on earth has the power to do this what the US does."
"ut as we know there is a difference between assuming something and having the prove. So now there can be legal actions concerning the spying. The American Civil Liberties Union now has the argument to claim against the government. Five years ago it didin't work because they couldn't prove the spying without judicial authorisation:
http://www.aclu.org/national-security/aclu-files-lawsuit-challenging-constitutionality-nsa-phone-spying-program"
" The US doesn't give a shit whether the Europeans are pissed off or insulted. Only the UK is their true ally and they don't give the UK more than a grudging "Keep it comin, fella".
The EU is the next Empire and the Yanks are running scared. Having failed so far to destroy our currency, their desperation escalates ..."
The FBI labeled Occupy a "domestic terrorist threat," and infiltrated it and sought to subvert it. Police brutality became a hallmark of the government's response to that movement. I'm sure the NSA is intercepting activists' emails, and reading them.
People like you are the last to come into the state's sights. But when you do, you'll click your heels and thank the authorities for hanging you."
// it was actually...
"U.S. is actually amassing troops in Australia as part of Obama's "piivot to Asia", and because Russia and China do not support the attempted U.S. coup in Syria, these are serious ramifications indeed. World War III is a bit more serious than temporary annoyance or embarrassment."
"No other country on earth has the power to do this what the US does."
"ut as we know there is a difference between assuming something and having the prove. So now there can be legal actions concerning the spying. The American Civil Liberties Union now has the argument to claim against the government. Five years ago it didin't work because they couldn't prove the spying without judicial authorisation:
http://www.aclu.org/national-security/aclu-files-lawsuit-challenging-constitutionality-nsa-phone-spying-program"
" The US doesn't give a shit whether the Europeans are pissed off or insulted. Only the UK is their true ally and they don't give the UK more than a grudging "Keep it comin, fella".
The EU is the next Empire and the Yanks are running scared. Having failed so far to destroy our currency, their desperation escalates ..."
"Up until now there has been little coverage in France. This has changed dramatically today. Every newspaper and TV station is talking about events now. Some are saying that political talk with the US Stasi is out of the question now and more to the point, legal action should be taken against them. Others who are equally outraged are demanding for the Statue of Liberty to be returned. How things have changed!
Snowden, stay safe. You're in our thoughts."
"Nice to see this getting traction..Maybe the Statue of Liberty needs to be placed on a barge so it can be towed to those countries who truly deserve it."
"like who? Ecuador? lol Who is France to judge, since when has France ever taken in the world huddled masses? They are the most xenophobic people on the planet."
"Nice to see this getting traction..Maybe the Statue of Liberty needs to be placed on a barge so it can be towed to those countries who truly deserve it."
"like who? Ecuador? lol Who is France to judge, since when has France ever taken in the world huddled masses? They are the most xenophobic people on the planet."
"The extent of your delusion is incredible. Are you seriously saying that other countries don't have spy networks? Tow the statue of liberty away by all means but put it where exactly? In one of the countries that do exactly the same as the US but if a Snowden came forward from those countries he would be dining on some radioactive sushi very quickly?"
"Least we forget MARKSTALLARD the result of the forensic examination of the corpse of the Palestine leader, Arafat, also seem to be a little overdue ? Talking about exotic foodstuffs, you understand."
todays friend is tomorrow's enemy.
today's enemy is tomorrow's terrorist
Today's terrorist is tomorrow's respected world leader..
So it will remain in Wikipedia, time by time someone anonymous will try to delete, change few links by few links, for up to point when someone notices, then will rest few years and...
There is a lot of information,that, if understood the background, potential, and real meaning, will be interesting:
Just really, near random links, that anyone can find with a minutes and start off their own string of research about what is done and what is happening, or had happened
https://en.wikipedia.org/wiki/Advanced_persistent_threat
"An advanced persistent threat is a set of stealthy and continuous computer hacking processes, often orchestrated by human(s) targeting a specific entity. An APT usually targets organizations and/or nations for business or political motives. APT processes require a high degree of covertness over a long period of time. The "advanced" process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The "persistent" process suggests that an external command and control system is continuously monitoring and extracting data from a specific target. The "threat" process indicates human involvement in orchestrating the attack "
https://en.wikipedia.org/wiki/Cyber_spying
"Cyber spying, or cyber espionage, is the act or practice of obtaining secrets without the permission of the holder of the information (personal, sensitive, proprietary or of classified nature), from individuals, competitors, rivals, groups, governments and enemies for personal, economic, political or military advantage using methods on the Internet, networks or individual computers through the use of cracking techniques and malicious software including Trojan horses and spyware.[1][2] It may wholly be perpetrated online from computer desks of professionals on bases in far away countries or may involve infiltration at home by computer trained conventional spies and moles or in other cases may be the criminal handiwork of amateur malicious hackers and software programmers.[1]
Cyber spying typically involves the use of such access to secrets and classified information or control of individual computers or whole networks for a strategic advantage and for psychological, political and physical subversion activities and sabotage.[3] More recently, cyber spying involves analysis of public activity on social networking sites like Facebook and Twitter.[4]
Such operations, like non-cyber espionage, are typically illegal in the victim country while fully supported by the highest level of government in the aggressor country. The ethical situation likewise depends on one's viewpoint, particularly one's opinion of the governments involved."
https://en.wikipedia.org/wiki/GhostNet
(YōuLíngWǎng) is the name given by researchers at the Information Warfare Monitor to a large-scale cyber spyingoperation discovered in March 2009. The operation is likely associated with an Advanced Persistent Threat).
https://en.wikipedia.org/wiki/Information_Warfare_Monitor
( (IWM) was an advanced research activity tracking the emergence of cyberspace as a strategic domain. It closed January 2012. It was a public-private venture between two Canadian institutions: The SecDev Group, an operational think tank based in Ottawa (Canada), and the Citizen Lab at the Munk School of Global Affairs, University of Toronto. The Principal Investigators and co-founders of the Information Warfare Monitor are Rafal Rohozinski (The Secdev Group) and Ronald Deibert (Citizen Lab). The Information Warfare Monitor is part of the Citizen Lab’s network of advanced research projects, which include the OpenNet Initiative, the Fusion Methodology Centre, and PsiLab. )
https://en.wikipedia.org/wiki/Citizen_Lab
(The Citizen Lab, opened 2001, is an interdisciplinary laboratory based at the Munk School of Global Affairs at the University of Toronto, Canada. Founded and directed by Professor Ronald Deibert, the Citizen Lab studies information controls—such as network surveillance and content filtering—that impact the openness and security of the Internet and that pose threats to human rights).
Psiphon is an Internet censorship circumvention that uses a combination of secure communication and obfuscation technologies (VPN, SSH, and HTTP Proxy). The Psiphon codebase is developed and maintained by Psiphon Inc which operates systems and technologies designed to assist Internet users to securely bypass the content-filtering systems used by governments to impose censorship of the Internet. Psiphon is specifically designed to support users in countries considered to be "enemies of the Internet".[1]
The original concept for Psiphon (1.0) was developed by the Citizen Lab
https://en.wikipedia.org/wiki/Internet_censorship
(Support for and opposition to Internet censorship also varies. In a 2012 Internet Society survey 71% of respondents agreed that "censorship should exist in some form on the Internet")
https://en.wikipedia.org/wiki/Hacktivismo#The_Six.2FFour_System
(Hacktivismo is an offshoot of CULT OF THE DEAD COW (cDc), whose beliefs include access to information as a basic human right. It was founded in 1999. The group's beliefs are described fully in The Hacktivismo Declaration, which seeks to apply the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights to the Internet. Oxblood Ruffin, the director of Hacktivismo, has argued forcefully against definitions of hacktivism that include web defacements or denial-of-service attacks. Hacktivismo has also authored its own software license agreement, the Hacktivismo Enhanced-Source Software License Agreement (HESSLA). The HESSLA prohibits use or modification that would violate human rights or introduce features that spy on the user.)
https://en.wikipedia.org/wiki/OpenNet_Initiative
(The OpenNet Initiative (ONI) was a joint project whose goal was to monitor and report on internet filtering and surveillance practices by nations. The project employed a number of technical means, as well as an international network of investigators, to determine the extent and nature of government-run internet filtering programs. Participating academic institutions included the Citizen Lab at the Munk Centre for International Studies, University of Toronto; Berkman Center for Internet & Society at Harvard Law School; the Oxford Internet Institute (OII) at University of Oxford; and, The SecDev Group, which took over from the Advanced Network Research Group at the Cambridge Security Programme, University of Cambridge. In December 2014 the OpenNet Initiative partners announced that they would no longer carry out research under the ONI banner. The ONI website, including all reports and data, is being maintained indefinitely to allow continued public access to ONI's entire archive of published work and data)
// etc, now click on. On related links, and on Wiki "Talk" page.
today's enemy is tomorrow's terrorist
Today's terrorist is tomorrow's respected world leader..
Todays's respected world leader is tomorrow's dictator ...
// And our open encyclopedia is full of information that You can combine, that gov and organizations does not want to delete or show remote interest publicly, for alerting and spiking off interest by confirming that is all terrible dangerously true.
Not the one I had in mind but agreed! :)
Today's drone victims are tomorrows enemy
_________________
Today's wanker is tomorrow's wanker.
"I assume the fax machine with the bug in it at the European Mission can be found in a nearby dumpster within a few hours of this publication, if not sooner. Will they send the bill for a new one to the U.S. State Department or the NSA?"
"
"I assume the fax machine with the bug in it at the European Mission can be found in a nearby dumpster within a few hours of this publication, if not sooner. Will they send the bill for a new one to the U.S. State Department or the NSA?"
"
They probably replaced the bug weeks ago anyway."
"
Get your facts straight:
http://ec.europa.eu/dgs/communication/take_part/myths/fact_033_en.htm
2000 more comments: https://www.theguardian.com/world/2013/jun/30/nsa-leaks-us-bugging-european-allies#comments
"
that is the fax they use when they want to send the usa a message
"
//yeah who uses fax in EU anyway...
"What's the point of spying on the EU? The Commission is obsessed with the shape of vegetables and the European Parliament is a rubber stamp institution. Got to be a dull job compared with spying on the Iranians or Chinese."
"Find out about trade deals, new regulations, financial problems, new investments, new laws, candidate members of the EU, new scientific and technical projects, deals with competitor nations ... the list is endless. The EU, as a whole, is one of the few blocs of nations that could potentially take on the USA politically and commercially. It would be a real advantage to the USA to get advance notice on any moves the EU is planning."
//to see how infiltrated it is by bad people and evil ideology. Measure average intelligence
"
//yeah who uses fax in EU anyway...
"What's the point of spying on the EU? The Commission is obsessed with the shape of vegetables and the European Parliament is a rubber stamp institution. Got to be a dull job compared with spying on the Iranians or Chinese."
"Find out about trade deals, new regulations, financial problems, new investments, new laws, candidate members of the EU, new scientific and technical projects, deals with competitor nations ... the list is endless. The EU, as a whole, is one of the few blocs of nations that could potentially take on the USA politically and commercially. It would be a real advantage to the USA to get advance notice on any moves the EU is planning."
//to see how infiltrated it is by bad people and evil ideology. Measure average intelligence
Get your facts straight:
http://ec.europa.eu/dgs/communication/take_part/myths/fact_033_en.htm
2000 more comments: https://www.theguardian.com/world/2013/jun/30/nsa-leaks-us-bugging-european-allies#comments
_________________
So it will remain in Wikipedia, time by time someone anonymous will try to delete, change few links by few links, for up to point when someone notices, then will rest few years and...
There is a lot of information,that, if understood the background, potential, and real meaning, will be interesting:
Just really, near random links, that anyone can find with a minutes and start off their own string of research about what is done and what is happening, or had happened
https://en.wikipedia.org/wiki/Advanced_persistent_threat
"An advanced persistent threat is a set of stealthy and continuous computer hacking processes, often orchestrated by human(s) targeting a specific entity. An APT usually targets organizations and/or nations for business or political motives. APT processes require a high degree of covertness over a long period of time. The "advanced" process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The "persistent" process suggests that an external command and control system is continuously monitoring and extracting data from a specific target. The "threat" process indicates human involvement in orchestrating the attack "
https://en.wikipedia.org/wiki/Cyber_spying
"Cyber spying, or cyber espionage, is the act or practice of obtaining secrets without the permission of the holder of the information (personal, sensitive, proprietary or of classified nature), from individuals, competitors, rivals, groups, governments and enemies for personal, economic, political or military advantage using methods on the Internet, networks or individual computers through the use of cracking techniques and malicious software including Trojan horses and spyware.[1][2] It may wholly be perpetrated online from computer desks of professionals on bases in far away countries or may involve infiltration at home by computer trained conventional spies and moles or in other cases may be the criminal handiwork of amateur malicious hackers and software programmers.[1]
Cyber spying typically involves the use of such access to secrets and classified information or control of individual computers or whole networks for a strategic advantage and for psychological, political and physical subversion activities and sabotage.[3] More recently, cyber spying involves analysis of public activity on social networking sites like Facebook and Twitter.[4]
Such operations, like non-cyber espionage, are typically illegal in the victim country while fully supported by the highest level of government in the aggressor country. The ethical situation likewise depends on one's viewpoint, particularly one's opinion of the governments involved."
https://en.wikipedia.org/wiki/GhostNet
(YōuLíngWǎng) is the name given by researchers at the Information Warfare Monitor to a large-scale cyber spyingoperation discovered in March 2009. The operation is likely associated with an Advanced Persistent Threat).
https://en.wikipedia.org/wiki/Information_Warfare_Monitor
( (IWM) was an advanced research activity tracking the emergence of cyberspace as a strategic domain. It closed January 2012. It was a public-private venture between two Canadian institutions: The SecDev Group, an operational think tank based in Ottawa (Canada), and the Citizen Lab at the Munk School of Global Affairs, University of Toronto. The Principal Investigators and co-founders of the Information Warfare Monitor are Rafal Rohozinski (The Secdev Group) and Ronald Deibert (Citizen Lab). The Information Warfare Monitor is part of the Citizen Lab’s network of advanced research projects, which include the OpenNet Initiative, the Fusion Methodology Centre, and PsiLab. )
https://en.wikipedia.org/wiki/Citizen_Lab
(The Citizen Lab, opened 2001, is an interdisciplinary laboratory based at the Munk School of Global Affairs at the University of Toronto, Canada. Founded and directed by Professor Ronald Deibert, the Citizen Lab studies information controls—such as network surveillance and content filtering—that impact the openness and security of the Internet and that pose threats to human rights).
Psiphon is an Internet censorship circumvention that uses a combination of secure communication and obfuscation technologies (VPN, SSH, and HTTP Proxy). The Psiphon codebase is developed and maintained by Psiphon Inc which operates systems and technologies designed to assist Internet users to securely bypass the content-filtering systems used by governments to impose censorship of the Internet. Psiphon is specifically designed to support users in countries considered to be "enemies of the Internet".[1]
The original concept for Psiphon (1.0) was developed by the Citizen Lab
https://en.wikipedia.org/wiki/Internet_censorship
(Support for and opposition to Internet censorship also varies. In a 2012 Internet Society survey 71% of respondents agreed that "censorship should exist in some form on the Internet")
https://en.wikipedia.org/wiki/Hacktivismo#The_Six.2FFour_System
(Hacktivismo is an offshoot of CULT OF THE DEAD COW (cDc), whose beliefs include access to information as a basic human right. It was founded in 1999. The group's beliefs are described fully in The Hacktivismo Declaration, which seeks to apply the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights to the Internet. Oxblood Ruffin, the director of Hacktivismo, has argued forcefully against definitions of hacktivism that include web defacements or denial-of-service attacks. Hacktivismo has also authored its own software license agreement, the Hacktivismo Enhanced-Source Software License Agreement (HESSLA). The HESSLA prohibits use or modification that would violate human rights or introduce features that spy on the user.)
https://en.wikipedia.org/wiki/OpenNet_Initiative
(The OpenNet Initiative (ONI) was a joint project whose goal was to monitor and report on internet filtering and surveillance practices by nations. The project employed a number of technical means, as well as an international network of investigators, to determine the extent and nature of government-run internet filtering programs. Participating academic institutions included the Citizen Lab at the Munk Centre for International Studies, University of Toronto; Berkman Center for Internet & Society at Harvard Law School; the Oxford Internet Institute (OII) at University of Oxford; and, The SecDev Group, which took over from the Advanced Network Research Group at the Cambridge Security Programme, University of Cambridge. In December 2014 the OpenNet Initiative partners announced that they would no longer carry out research under the ONI banner. The ONI website, including all reports and data, is being maintained indefinitely to allow continued public access to ONI's entire archive of published work and data)
// etc, now click on. On related links, and on Wiki "Talk" page.
https://en.wikipedia.org/wiki/Censorship_by_country
https://en.wikipedia.org/wiki/Internet_censorship_and_surveillance_by_country







No comments:
Post a Comment
Seega kuidas siis nii on.. anna meile teada
So let us know.. how is it..
Margus